案例:Secure Home Access
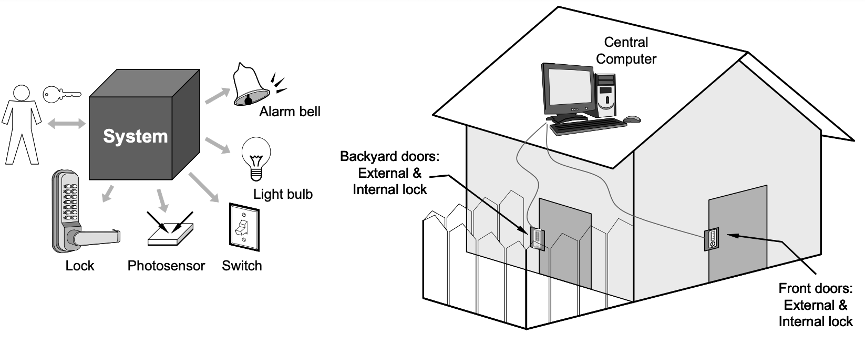
Secure Home Access: the system offers house access control using a central computer.
1. Requirement Description#
The “Secure Home Access” system could be required to authenticate (“Are you who you claim to be?”) and validate (“Are you supposed to be entering this building?”) people attempting to enter a building.
Our first case-study system provides several functions for controlling the home access, such as door lock control, lighting control, and intrusion detection and warning.
2. Requirement Modeling#
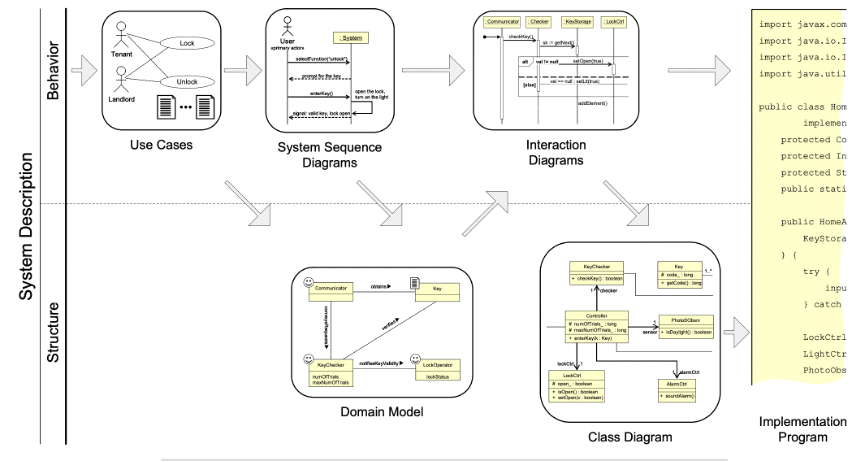
The summary of a single iteration of the software development lifecycle.
3. Use Case Diagram#
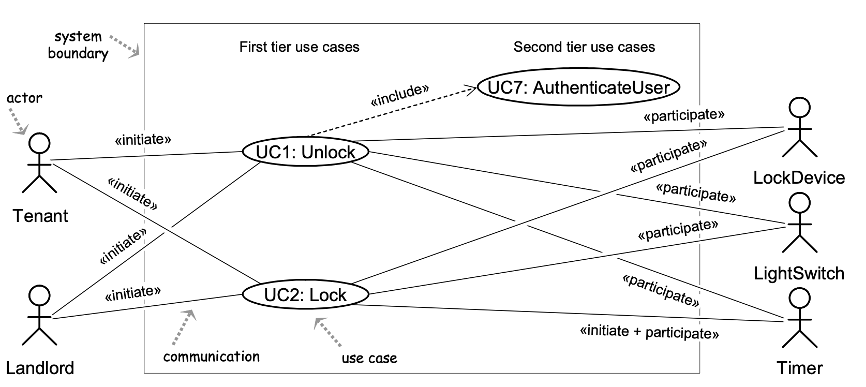
The UML use case diagram for the device-control subsystem of the home access system.
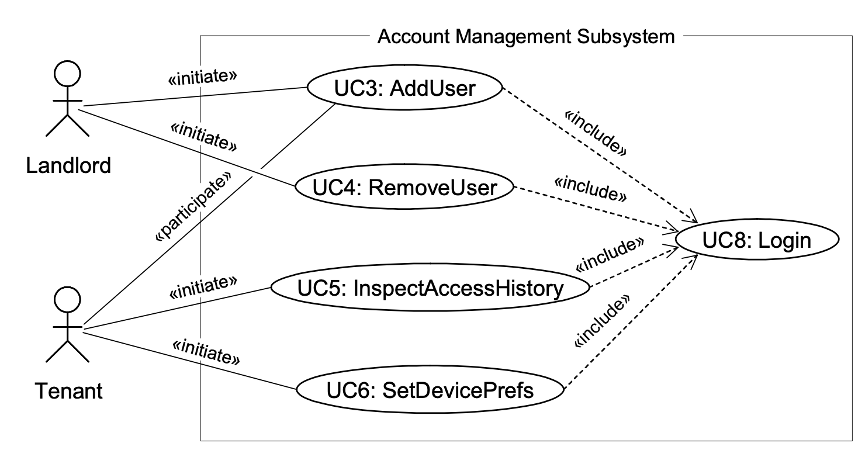
The Use cases for the account-management subsystem of the home access system.
4. System Sequence Diagrams#
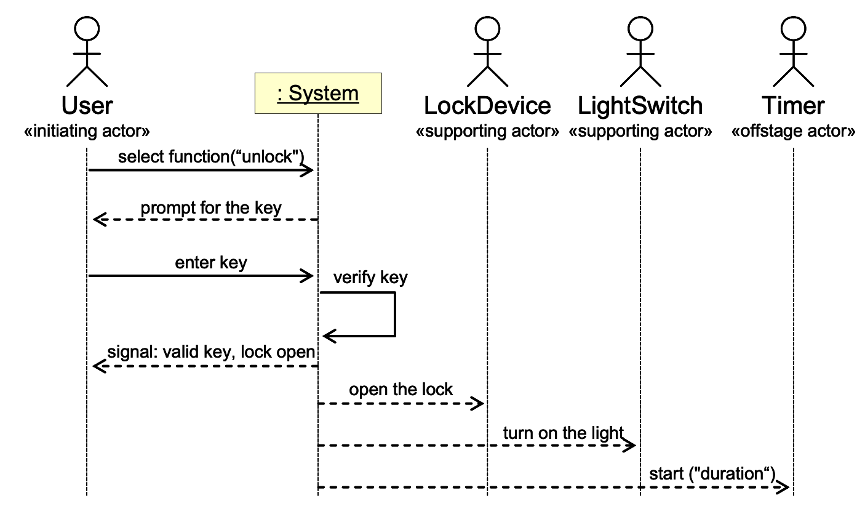
The UML System sequence diagrams for the Unlock use case.
Main success scenario
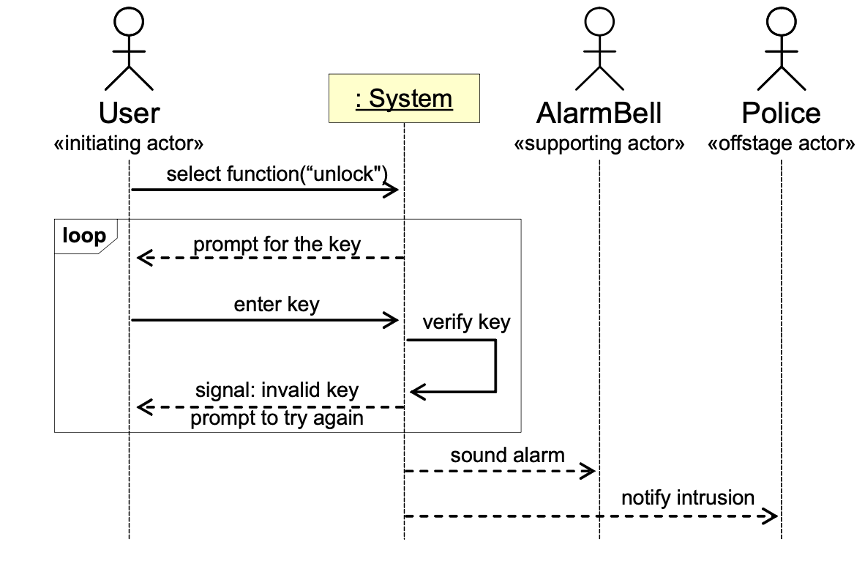
Burglary attempt scenario
5. Designing Object Interactions#
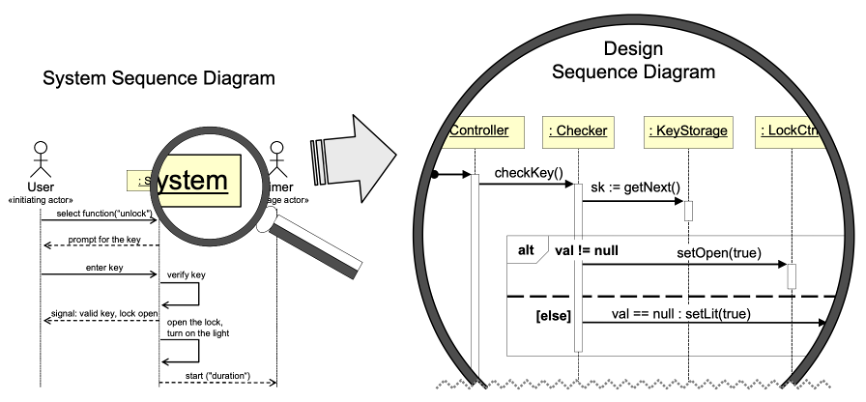
From system sequence diagrams to interaction diagrams: the magnifier glass symbolizes looking at interactions inside the system.
6. Sequence Diagrams#
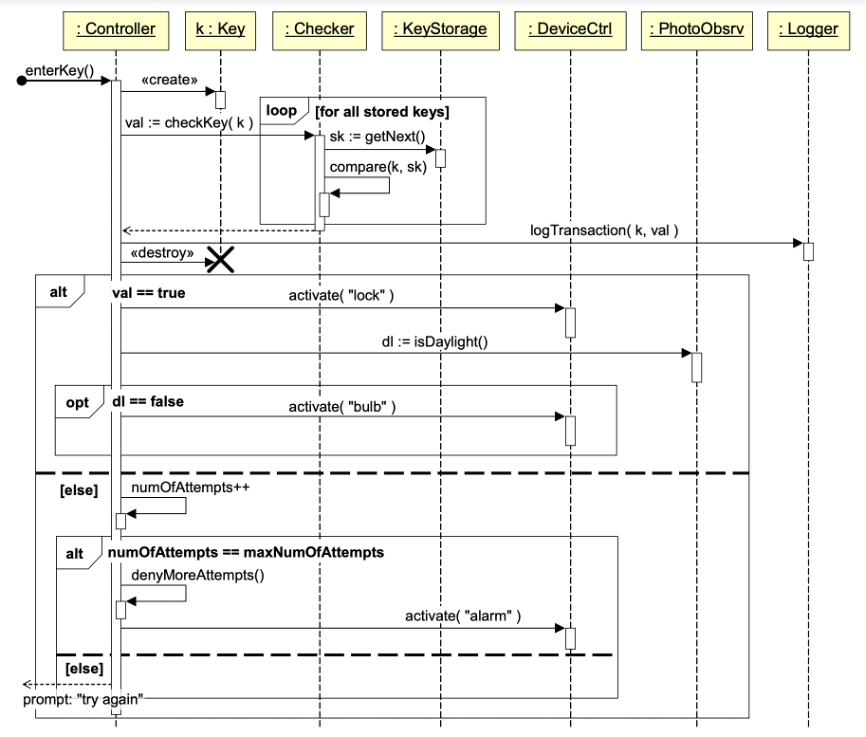
The sequence diagram for the system function “enter key”
7. Class Diagram#
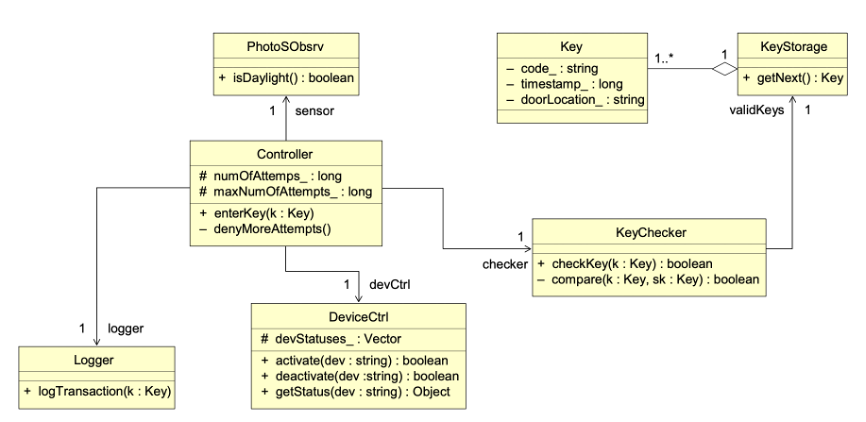
Class diagram is created simply by reading the class names and their operations off of the interaction diagrams.
8. State Diagram#
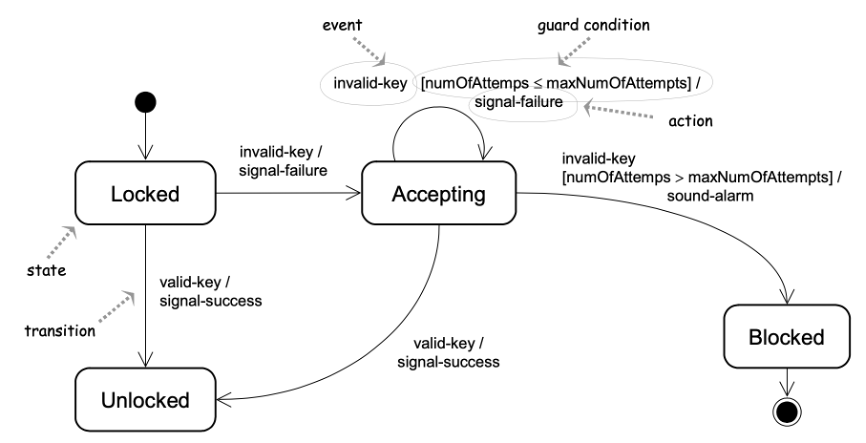
The UML state diagram for the Controller class.
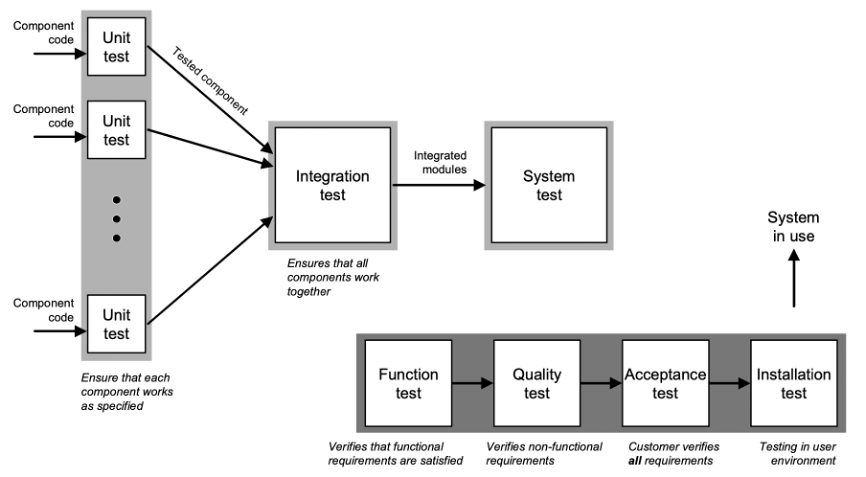
9. Software Testing#
Testing is usually guided by the hierarchical structure of the system as designed in the analysis and design phases.